New Wordpress Hacking Strategy Using Cloaking to Target Google IP Addresses
Stay Protected
An ounce of prevention is worth a pound of cure.
If you want to prevent any of your Wordpress blogs from getting hacked make sure you keep your software up to date, and follow other basic Wordpress protection strategies, like - securing your admin folder, removing the Wordpress version number from your theme's header.php file, creating an index.html file in your plug-ins directory, and removing other common Wordpress oriented footprints like a "powered by Wordpress" signature in the page footer.
Get an Early Warning
Another thing you can do to protect yourself is to get an early warning if/when your blog does get hacked. You can subscribe to a Google Alert for site:yoursite.com viagra OR cialis OR levitra, and so on...as Patrick explains on Blogstorm.
If one of your blogs gets hacked fix the others before it is too late. Some plug ins make it easy to update/re-install Wordpress.
Stopping Comment Spam
Not quite as bad as full hacking, but comment spam is still annoying. There are a couple good plug ins to help prevent comment spam as well, including Akismet and Spam Karma.
Other easy suggestions on this front are to require a captcha and force first time comments to be moderated before appearing on the site.
Google IP Address Targeted Hacking + Cloaked Spam
One of my blogs was recently targeted by a blog hacker that inserted links into the site that could *only be viewed by GoogleBot*. You typically would not notice such a hack unless you subscribed to a Google Alert for your site, saw yourself ranking for some of the spam terms, and/or when your Google Search Traffic started to fall.
The issue with such a hack is that it is hard to know if you wiped it out, even if you update everything. When you use Firefox's User Agent Switcher you still will not see the links because you are not surfing from one of GoogleBot's IP addresses.
In fact, for this particular hack you can't even see the links on Google's cached version of a page unless you view the text cache version of the page.
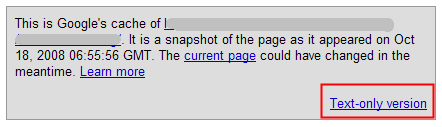
Once you click the text only cache link tons of pharmacy links appear in the page footer. This screenshot was taken from a Texas Instruments blog post on security and safety
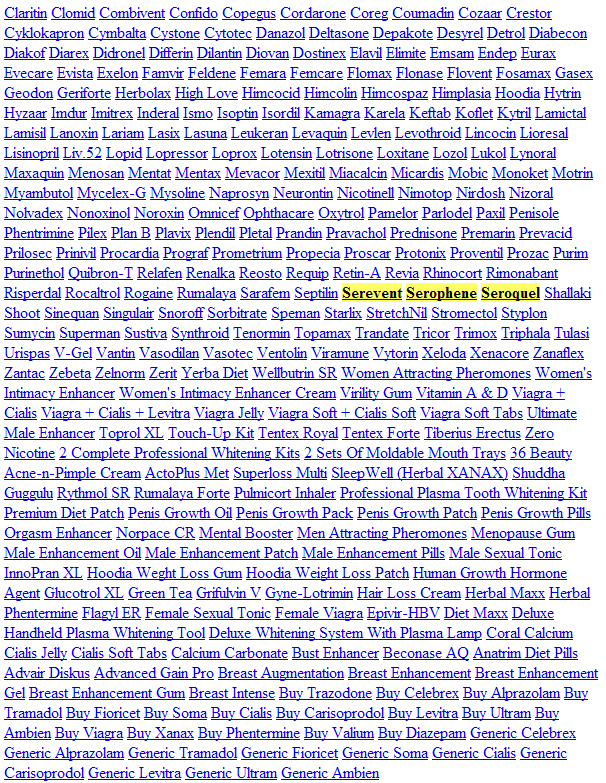
Google currently has indexed over 20,000 pages with this particular hack.
How This Type of Hack Influences Google Traffic
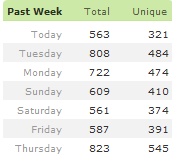
Earlier this week one of my writers who loves blogging complained that search traffic was dropping slightly, and then after a few days of minor decay the search traffic was cut in half. Keep in mind this site gets much of it's traffic from organic links.
Our Google traffic started to fall off slowly, and as more of the pages with spam in them got indexed the fall off became sharper. After a week or so traffic may be a small % of what it was...or if they just spam a couple pages the change in traffic may be so minor that you never notice it. The traffic decay rate depends on...
- the crawl priority of your site (how frequently it gets crawled)
- the number of pages you have on your site
- how bad your site gets spammed (number of spammy links and pages, etc.
You can see what portion of your site got hit by searching Google for "spammy footprint" site:example.com and comparing that count to the total number of pages Google shows indexed for site:example.com.
How to Clean Up Your Wordpress Blog
Regular updates are a plus to make it easy to revert to a prior version if needed. And if you find yourself upgrading software after a hack make sure your server is clean (save old files elsewhere) and install fresh. You probably want to change your database and Wordpress passwords after upgrading, and if you are not sure where the hack was you may also want to change your theme.
There are a lot of different ways people can hack into a Wordpress blog. Some spam hunting ideas include...
Using SSH to look for recently modified files and/or weird new files that were added to your site. Some hackers may also add files to the root of your site, or above it hidden somewhere on your web server.
Some hacks may be via a Wordpress plug-in. If you have inessential plug-ins installed see if others have complained about them getting hacked, and see if you can remove them. I think some hackers that get into Wordpress go so far as adding plug-ins that position spam throughout the blog.
If your database contains spam in it then you can run the following MySQL query (from Michael VanDeMar) to find many of the most common types of Wordpress link hacks.
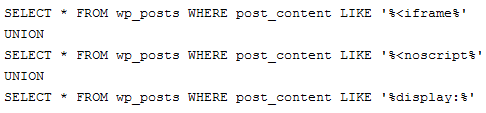
If you can't find any spam in your Wordpress database, then...
- look for files that have been added or modified
- back up your files and database
- disable plug ins
- delete all files (except for maybe your config file and .htaccess file - and verify those have not been edited as well)
- update your blog to the newest version of Wordpress
- change your MySQL password and your Wordpress password
- install a new theme
- download necessary plug-ins from their original sources if you want to keep using them
- make sure you performed all the steps at the top of this article to try to keep your blog safe.
- if your problem was a shoddy host that got compromised then its a good idea to shift to a better Wordpress hosting solution
If The Hacker Was Using IP Cloaking...
If the hacker was using IP cloaking you can't be 100% certain that the spam is gone until Google tries to index new pages on your site and/or re-indexes old pages that were hacked.

You can find files that have been indexed in the last day or last week by using Google's date based filters.
If you updated your blog a few hours ago you can also do a regular site:www.example.com search on Google and set the results to 100 per page to find any pages that have been re-indexed in the last few hours. Once the search results come up you can search the search results page for hours ago.
One note of caution is to check the actual page's cache date at the top of the page. Sometimes when a cache is really new clicking on the link will show you the new page, but sometimes it will show you a cached page from a few days back. When you see a new cached page without the spam links hopefully your spam problems are almost over and your site is on the road to recovery, with rankings improving as Google caches more pages from your site.
Remember to set up a Google Alert for your site so you can track if any spam links magically re-appear.
Your Turn
I have only had a couple blogs hacked in my many years of blogging. Did I miss any obvious tips and/or wisdom you can add to the above post?




Comments
A wordpress blog of mine has been hacked too. I found some hidden CSS links. Don't know how is has been hacked. Updated the version
We had a WP blog set up as a side blog on a Drupal based CMS site (I know, I know...). Somehow the hackers got in, and not only hacked the WP blog, but also added malicious links to our Drupal template. Then, they somehow got onto other sites in the same hosting account (static html) and injected the links there as well. 5 of our sites that got hacked got penalized in G - only 2 had WP installed.
After losing 80% of our income for that month (August), we cleaned everything up, split the domains into their own hosting accounts (a recommended security feature not mentioned), and filed a reconsideration request.
TG everything is back to normal now...
QUESTION: Is it illegal/immoral to form an "anti-hacker" consortium to take donations to hire a "professional" to find these hackers, and take care of them? I lost over $8K to these hacks - I'd be willing to donate another $1000 to find the hackers that stole my money.
Is Drupal subject to such hacks as well?
It has a smaller and more sophisticated userbase, so it is not attacked quite as often as Wordpress is.
I am not sure if it is unethical, but I would like to donate to the cause.
I also saw one sleazeball uploaded a script that gave them access to anything, created an admin account on one of my blogs, and set cookies to force exit if one tried installing an update...sooooo sleazy!!!
this is a useful tool for those who do not know some of Google's advanced search and cache behaviors
http://www.seoidiot.co.uk/cachechecker/
Yeah, that's why I recommend doing a complete wipe and reinstall, instead of using automatic upgrade, if you've already been hacked. Something they'll leave stuff that you won't see, and that does let you upgrade... but let's them right back in again.
Aaron, sorry you got hacked. Every time it happens to me it seems like it's because I didn't listen to my friend Donna when she tells me to upgrade. :P
Mind if I ask which version of WP you were running? 2.5.2 was a security upgrade, so I already know nothing below that was safe... but if this is new it would be worth getting the word out. Thanks.
Aaron, your article inspired me to write a blog on "Why Hackers Should Not Hack WordPress Blogs".
Please do read – its an interesting read.
Dilip Shaw
There was a lot of misinformation in that article Dilip. For instance "Inbound links from irrelevant site won’t help your site get better ranks in search engines" ... the spammers wouldn't be hacking so many blogs *unless* they saw a ranking boost and there was a potential return.
Aaron,
This debate is going on since seo was born. However I have some pointers straight from Google, and I believe this is what they are trying to say.
http://www.google.com/support/webmasters/bin/answer.py?hl=en&answer=66356
http://www.google.com/support/webmasters/bin/answer.py?hl=en&answer=66736
What I feel is hackers hack for the joy of hacking and not necessarily for SEO purposes. They spend a lot of time learning new methods of hacking, and less time on reading some basic SEO tips. I think most of them have a notion that getting more inbound links from any site will help, without realizing that both sites (the hacked and the hackers’) might be harmed.
When looking for a doctor whose advice will you take?
a) a pharmacist referring you to a doctor, or
b) a banker referring you to a doctor.
When looking for a mutual fund to invest whose advice will you take?
a) a banker's advice on mutual funds, or
b) a pharmacist's advice on mutual funds.
If there is in any other misinformation please do let me know.
Thanks.
Google likes to appear more omniscient than they are.
I went and spot checked 40 or so in the query you showed, and of what I saw only 1 of them was above version 2.5.1, with most being much older. More surprising than the number of them affected, really, is that it didn't happen to them sooner.
With the one I did see that was a "safe" version, it was 2.6. They may have upgraded after they were hacked, though, and left a backdoor. Hard to say without knowing more... if they were hacked before they upgraded, they may not have even known about it. Wordpress is designed for the non-tech savvy to be able to have their own blogging platform, so a large portion of the users don't even realize that they should be careful of hackers till someone else tells them that their blog has been hacked.
How could you tell what versions they were using Michael? Were you looking at the generator # that is part of header.php?
Yes. Almost all of them did not remove it. I know that can be spoofed... but considering they were hacked, and the versions that they were all displaying (aside from one, as I mentioned) were hackable, I am taking the tags at face value.
Were any of yours that got compromised 2.5.2 or 2.6, if you don't mind me asking?
I think one of them was 2.5.2...but there are probably more to look through and fix still :(
Aaron,
While I am sorry that your WP installs got hacked, it does make me feel a whole lot better about my own recent experience with the same exploit. So it's happening to everybody, even gurus.
I have since set up the suggested Google Alert, but noticed the problem when my healthy Google traffic fell off a cliff in a few days. Looking at the site: stats and the cache dates, I instinctively checked the text-only version that found the dreaded links.
I used the WP exploit scanner plugin, MySql queries and the SSH methods and *hope* I have finished it off with a new install.
The good news is for anyone else that suffers from this is, after a reconsideration request to Google, the site was re crawled and being served up "correctly" in a few weeks. Still a lot of revenue and visitors to lose, though.
Actually, I was wrong about 2.5.2, especially since there never was a version with that number. :)
2.6.2 was supposedly the secure version, with a known exploit in every previous version up till then... until today, that is, when a new exploit was discovered:
New Security Release for Wordpress
So, now the "safe" version is 2.6.3. Off to go update before I get hacked.
Thanks Aaron!
My sites were also hacked using cloaking, but fortunately they were detectable using user agent switching in firefox.
My .htaccess file was modified, but it wasn't easily detectable as there were many blank lines between what looked like the end of the file and what was actually the end of the file.
To find out if your plugin maybe a security risk you can go to http://blogsecurity.net/wordpress/blogwatch/blogwatch/
I would also recommend the Wordpress login Lockdown (http://wordpress.org/extend/plugins/login-lockdown/) as it stops brute force attempts to guess your password by locking an IP address after a few attempts (you can set the no of minutes)
You may also want to try WPIDS for intrusion detection - see http://php-ids.org/2007/09/12/wpids-phpids-your-wordpress-the-comfy-way/
Heh. I like the comment about tracking these guys down.
I once spent close to a year tracking a guy down that kept attempting to hack our site and get our PayPal account closed.
I put the word out wherever I could and put a bounty on getting his contact details. Eventually it paid off and I got a name. From there I found out that he was 16, lived with his Mom in Germany and worked during the evenings in a video rental store.
Some German friends of mine started calling him at work, and soon after that the threats against our site stopped. Result!
I love stories like that...people think they are soo kewl and then they get tracked down in the real world.
These wankers need some rock salt and a shotgun used to straighten them out.
Pretty funny that the geek web guy now sounds like a farmer ;)
Hi Aaron,
Thanks for the tips, currently running through the list for a client, so much appreciated!
Ben M
You guys rule. I am way too naive about hacking - have only had one site hacked in about 6 years, and it was an obvious, easily fixed server hack. You have made me a little nervous, rightfully so, and all of my Wordpress stuff will be stronger as a result.
Kudos to all - this is a very valuable thread to me, and the comments are great.
Another thing that is common, as noted by my friend Joost, is also some people edit a theme's 404 error page to make it do 301 redirects, then point a few links at the hacked 404 theme page.
I am not sure if I mentioned it above, but also many of the people who hack in give themselves an adminsitrator's account in your Wordpress database as well.
And some of them make the hacked theme files hard do delete by setting the permissions to 444 or something like that...you can use something like Putty or Leech FTP to change permissions/CHMOD those files to 777 or something like that so you can delete them.
Your 'Google Alerts' tip to identify Wordpress injections is pretty damn kewl. Although I use Google Alerts regularly, I never envisaged using it in this manner.
Recently our company site was hit by a Wordpress attack similar to the vulnerability you describe above. Apparently it was variant of the Goro spam injection attack.
Linux by Examples has a decent tutorial for clearing up the aftermath and protecting yourself against this type of attack.
I'm surprised that google webmaster central doesn't already have a robost method to indentify potential spam problems/links/words/phrases on a website.
Seems like a pretty obvious and useful tool for both sides.
ie instead of having to use google alerts; because there are potentially 10s of thousands of potential spammy keywords you could have a tool that detects from a master list and measures everyones site.
Google is piloting such an initiative, but its best to actively protect yourself as well.
Digressing slightly but related to WP hacks - if and when that happens, it's a lot less painful when you have a current backup to rely on, or better still, a series of backups.
The problem with the built-in WP backup is that you have to remember to click the 'backup' link every now and then.
There are a few plugins which automate the process and schedule them automatically - even sending a gzip backup of the database by email.
The one which works best for me - I guess I've a typical WordPress environment of linux shared hosting with cpanel- is WP Database Backup: http://www.ilfilosofo.com/blog/wp-db-backup
Just works a treat.
On the subject of other useful security plugins - here's what I have installed:
Thanks for that fatdiver :)
Here is an image of some bogus plug ins that some of the hackers added too
http://www.seobook.com/images/bogus-plugins.png
I also saved a text file of garbage that they put in the themes directory
I'm surprised none of you have mentioned the plugin bad behavior. It blocks PHP attempts to your site and has kept me from getting a lot of those zillion link comments in the first place, then Askimet gets what few slip through.
ê¿ê
Hey Aaron,
So it turns out that I actually do rank for Cialis or rather I have a page that contains it. Can't see it in text only cache. What do you suggest? Does deleting those pages help? It's like 5 pages...
Aaron,
I'm running WordPress for a corporate blog and use datapresser for rank checking/recording of back links and noticed that hundreds of p=12345 high number post counts are showing up as back links and I am afraid that this could be a sign that the blog has been hacked. I am unable to retrieve the text-only version of the cache and have tried out all of the user agents that I could find and nothing showed up... Today I setup Google Alerts and haven't seen anything thus far. Would you mind contacting me if you have anything else I could try or could you post it here publicly? See you at PubCon.
You could try visiting those pages and see what happens. Also see if any of those pages exist on your server.
Beyond that it gets much more complex.
Great post! Great topic! I just learned the following today and was wonderingif you knew of this technique.
My blogs were recently hacked, I think. It hasn't been confirmed by support yet, but all my blogs disappeared- with only the install page in it's place. In C-Panel, all my files were present, but all my databases were empty!
I found a video on a popular video site about how to get the admin's password for a WP blog. Looks like the blog is only vunerable if an Admin publishes a post. So, that's what they look for admin blog posts.
I set up another user for myself as an author, just for making posts.
Keep up the good work,
Kathy Pop
There are probably lots of different hacks and hackers beating up poor Wordpress users. Thankfully I have not suffered from all the wide variety of them...just a few so far.
It looks like Google traffic and rankings are coming back up to around normal levels...11 days after we fixed the issue.
I am thinking of extending that tool to allow automated checks of a batch of sites against probable spam links inserted. With a warning email to any site that needs to check.
Thanks for the link btw, hope it was useful. It is certainly easier than explaining how to do the check properly to most bloggers :)
There will always be a figth between hackers and good guys. Even a special law can kill illegal methods.
Keep up working guys.
Add new comment